Vulnerable packages on FreeBSD: pkg audit
This article has last been updated at .
FreeBSD is definitely another beast than Linux. In some areas, FreeBSD is really a powerful operating system. Package management is maybe not the first one you may think of. Typically FreeBSD users have two options when it comes to installing packages.
Auditing FreeBSD with pkg audit
Ports collection
The ports tree allows the administration to build software they need, with the compilation flags he or she prefers. This makes the software optimized and typically the last versions are available. The downside is in the overhead of compiling software, especially with multiple systems involved.
Using binary packages
Like Linux systems, the concept of precompiled binaries is available to FreeBSD as well. These binaries are packaged together with configuration files, data files, and documentation. Easy to use, to update, and remove. The downside is less customization possibilities.
If you use the package manager ‘pkg’, you can use the same utility to perform a security scan.
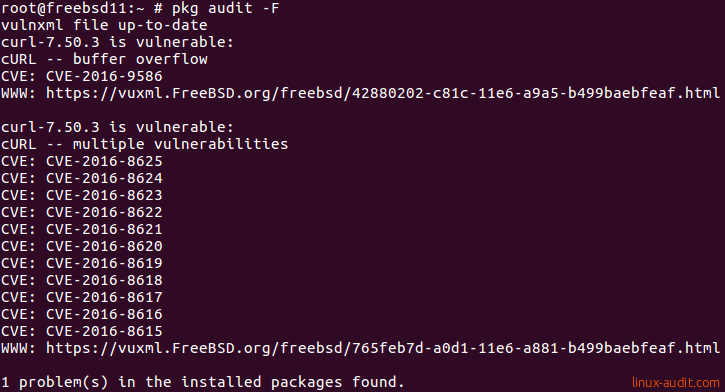
pkg audit -F
The pkg audit command will show details about the vulnerability database vuxml
and finally any installed packages that are known to be vulnerable. Where available a CVE number is added, which is a unique identifier for software vulnerabilities, together with a link for more information.
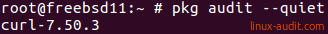
To only get the package names use the -quiet (or -q) option. Optionally use the -F if you want to refresh the vulnerability data again.
pkg audit -q
This option is great for automated solutions. We use this one in our auditing tool Lynis, to see what packages are vulnerable and count them.
Are you using other tools on FreeBSD to check for vulnerabilities? Let it know!

