Vulnerabilities and Digital Signatures for OpenBSD Software Packages
This article has last been updated at .
If you audit systems on a regular basis, you eventually will come across an OpenBSD system. OpenBSD is known for its heavy focus on security, resulting in an operating system with a low footprint and well-audited source code.
While most operating systems are pretty secure, they quickly will introduce new security holes when installing external software components. Although OpenBSD does careful checks for packages they add, those might be containing still a vulnerability, waiting to be discovered. So in this article we have a close look at dealing with packages and what to look for when auditing them.
OpenBSD Software Packages
Packages versus Ports
OpenBSD has the ability to install a package or a port. The latter is nothing more than a smart reference to the original source file, completed with operating system specific patches. This enables the system to actually successfully build the program.
Packages on the other hand, are precompiled binaries, with configuration files and installation instructions. In this case the package manager knows exactly where to place each file and with what permissions.
OpenBSD advices users to use packages, as they are optimized and carefully examined. Besides that, it will limit the hassle users might have getting ports compiled, due to changes in the operational environment. The smallest change in a default compiler option might influence its behavior, which are better tailored for the dedicated people who build the packages.
Vulnerability Scanning
OpenBSD does not maintain a specific vulnerability database, like for example NetBSD does. However to determine what (security) updates are available, it is wise to follow the related mailing lists, and simply stay up-to-date with software packages.
Checking for patches can be done via the pkg_add utility. Use the update mode (-u) and don’t allow it to actually do the update (-s). The -x and -I are for non-interactive display and mode.
pkg_add -Isxu
Note: this will only work for snapshots, and upgrading between releases.
Digital Signatures
Starting with OpenBSD 5.5 the tool signify was introduced. The name is a combination of “sign” and “verify”. So it is no surprise that its goal is to sign and verify OpenBSD releases, includes underlying components like packages.
Signify components
To allow OpenBSD software packages being signed and verified, they are split into two phases. In the first phase a package maintainer builds the package. Then the package is signed with a secret key (private key). When a user wants to install the related package, the linked public key will then be used to verify the digital signature. If it matches, installation continues. If not, the installation is aborted.
Public keys
OpenBSD distributes the keys packaged with the base system itself.
# ls -l /etc/signify/*
-rw-r-r- 1 root wheel 104 Aug 8 08:05 /etc/signify/openbsd-55-base.pub
-rw-r-r- 1 root wheel 108 Aug 8 08:05 /etc/signify/openbsd-55-fw.pub
-rw-r-r- 1 root wheel 108 Aug 8 08:05 /etc/signify/openbsd-55-pkg.pub
-rw-r-r- 1 root wheel 104 Aug 8 08:05 /etc/signify/openbsd-56-base.pub
-rw-r-r- 1 root wheel 108 Aug 8 08:05 /etc/signify/openbsd-56-fw.pub
-rw-r-r- 1 root wheel 108 Aug 8 08:05 /etc/signify/openbsd-56-pkg.pub
-rw-r-r- 1 root wheel 104 Aug 8 08:05 /etc/signify/openbsd-57-base.pub
-rw-r-r- 1 root wheel 108 Aug 8 08:05 /etc/signify/openbsd-57-fw.pub
-rw-r-r- 1 root wheel 108 Aug 8 08:05 /etc/signify/openbsd-57-pkg.pub
These files represent the base system, firmware, and packages.
Checks in pkg_*
To properly use digital signatures, they should be used before actually installing new components on the system. So the utility pkg_add got extended to do these checks. Next in line is pkg_info, which got a new -C option to show the digital certificate information as well. The result of using this option is a small line stating “reportedly signed by” followed by the name of the public key.
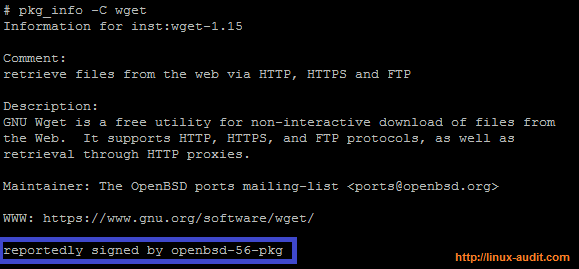
Digitally signed software in OpenBSD pkg_info
Signify tool
Another option is using the signify tool directly. For example when downloading new files, use the related key and signed hash file to verify the file integrity.
# ftp ftp://ftp.eu.openbsd.org/pub/OpenBSD/5.6/amd64/{bsd,SHA256.sig}
# signify -C -p /etc/signify/openbsd-56-base.pub -x SHA256.sig bsd
Signature Verified
bsd: OK
Conclusion
OpenBSD is known for its security and it was actually a surprise that signed software was only introduced in OpenBSD 5.5. But now we have this available, the chain of package release, up to installation can be checked more easily. This is definitely another good step to keep systems secure!

