Using File ACLs on Linux for Additional Security
This article has last been updated at .
File ACLs can increase security due to the more granular permission structure. Still the use of ACLs is often not known to system administrators, resulting in directories and files having inappropriate file permissions.
When to use (example)
A directory could be configured with very tight permissions, including a proper owner and group. Normally the “Other” (everyone) group would have to be used to open up the file for people outside the owner group. This has a serious downside to open up a directory or file contents for all users.
With ACLs we can solve this issue. We still apply the tight permissions, however additionally we can give a single user file access.
Getfacl
To see the existing file permissions, the getfacl command can be used.
# getfacl test1
# file: test1
# owner: root
# group: root
user::rw-
group::r-
other::-
In this particular case the file has read-write permissions for the owner (root) and read access for the group (root).
Setfacl
When we want to allow the user “www-data” to access this particular file as well, we can adjust the ACL with the setfacl command.
setfacl -m u:www-data:r test1
This command adjust the file ACL and modified it to the user “www-data” having read access to the file, as can be seen in the screenshot below.
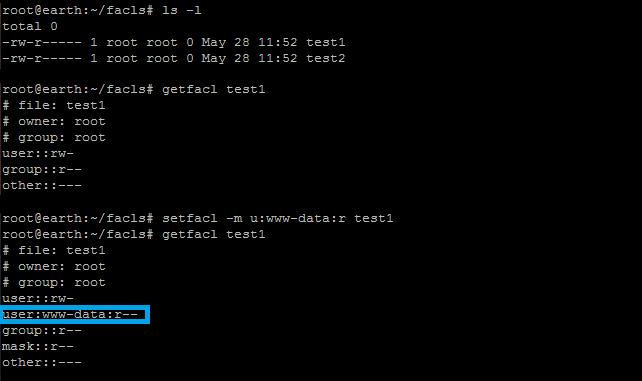
The use of getfacl/setfacl under Linux to apply file access control list.
Plus sign in ls output
If ACLs are applied to a file, the ls output will change. An additional plus sign will show up at the end of the line. This is to avoid overlooking the use of these additional permissions.
# ls -l
total 0
-rw-r--**+** 1 root root 0 May 28 11:52 test1
-rw-r-- 1 root root 0 May 28 11:52 test2
Conclusion
File ACLs are powerful and provide a system administrator with more granular access possibilities. Where possible, use this feature to apply more strict file access, yet allowing the right people and process to access data.
