Upgrading External Packages with unattended-upgrade
This article has last been updated at .
The unattended-upgrade tool is a great way to keep your system automatically updated. While you might not always want to do that for all packages, it definitely can be a great way to assist in your security efforts. In that case, tell it to track security updates and install the related packages.
If you are using third-party packages (e.g. via PPAs
), the system has no idea about security updates for those packages. So you need to take an additional step and get them included manually.
Determine the PPA Origin and Suite
The first goal is to determine the details from the PPA (or other external package type). This can be done by peeking in the /var/lib/apt/lists directory. Use the related files ending with InRelease, to see more details about the specific package.
less /var/lib/apt/lists/ppa.launchpad.net_nginx_development_ubuntu_dists_trusty_InRelease
For our nginx package we get this output below.
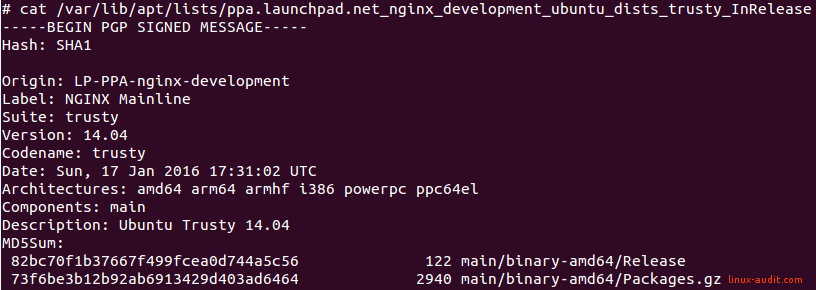
The two things we need from this file is the field Origin and Suite. These two strings have to be combined and provided to unattended-upgrade. It then understands that this PPA should be upgraded automatically.
Change Configuration File
vi /etc/apt/apt.conf.d/50unattended-upgrades
In this case, we add nginx to the Unattended-Upgrade::Allowed-Origins section.
“LP-PPA-nginx-development:trusty”;
So the result will look something like this:
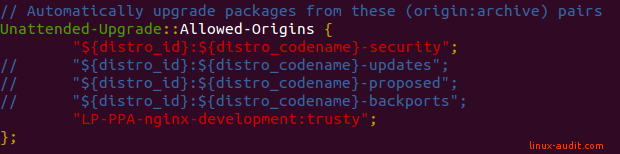
The hardest part has been completed!
Perform Automatic Upgrade
When the changes have been made, check the new configuration. Run unattended-upgrade in dry-run mode. Add the debug flag to see more details.
unattended-upgrade -dry-run -debug
If there is an update available, which you can check with apt-get upgrade, then it should show up. If not, your might have a typo or mismatch in your repository name.
Additional Tips
Sometimes it is good to run a development version, especially if you need the feature set. Keep in mind that those packages are not part of the security channel. So additional upgrade attention for these packages is strongly advised. Better safe than sorry!
The unattended-upgrade tooling can’t always upgrade packages. This is especially the case when configuration files are changed. And you guessed it right, this happens a lot to development packages. So if you have the chance, set up additional monitoring for any upgrades. Don’t simply rely on the existence of unattended-upgrade, and have a second tool or script test the availability of updates.
