Unused Linux Users: Delete or Keep Them?
This article has last been updated at .
We get often the question what one should do with unused users on Linux. Everyone who looked in the /etc/passwd file will recognize them, strange usernames. A great example is UUCP, or Unix-to-Unix Copy. Once used for communication on direct lines, now another piece of history in our password files.
The Options
Before we make any decision on dealing with unused Linux accounts, we should look at the most obvious choices we have. The options include:
- Keep them
- Disable
- Delete
Keep the account
The first option is the easiest. Simply take no action and keep the users in the file. While this is a totally valid strategy, it might not be the best option. One reason for this is pollution in the passwd file. It might give room for “hidden” accounts, especially between legitimate non-personal service accounts (like www-data).
Disable the account
Next option is to disable each account that is not used. Disabling can be done in different ways.
Option 1: Change the password
Changing a password is done with the passwd utility. To change the password of another user, you will need root permissions.
passwd username
This option is very basic. Although it does make sure a user can not log in without knowing the new password, public key authentication via SSH is still possible.
Option 2: Set an expiry date on the account
A slightly more advanced option is to mark the account as expired. This way the user can’t log in with a known password, nor with public key authentication.
chage --expiredate 0 username
The beauty of this is that accounts can be disabled, without their password being touched. The second positive thing to remark is the clear message an user gets when trying to log in.
Your account has expired; please contact your system administrator
If we would like to activate the account again, we give it an expire date of -1, which means never.
chage --expiredate -1 username
A few tips
- Use -E as short version of -expiredate
- Use chage -l (or -list) to see information about an account
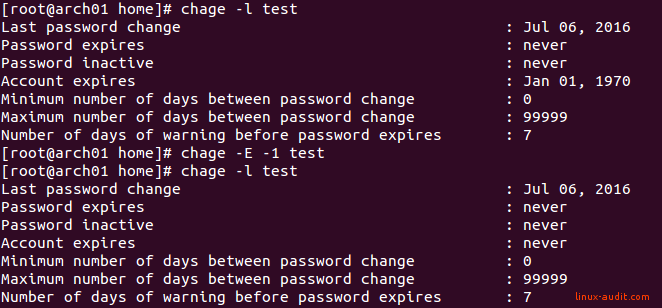
Using chage to expire and unlock accounts
Option 3: Lock the account
You can also lock an account with the usermod utility. It is also advised to change the shell to /bin/nologin.
usermod -lock -expiredate 1 -shell /bin/nologin username
This will make impossible to log in, similar to using chage. Unlocking with usermod is also still possible.
usermod -unlock -expiredate 99999 -shell /bin/bash username
Delete Account
The last option is making serious changes to the system and delete unused accounts. The LSB specification
states that some accounts are optional. Distributions usually simply add the accounts, to account for all users. That doesn’t mean you should keep them on your systems. For example Arch Linux took serious measures and removed most of the unused accounts by default.
Check password files
If you feel you are ready for the task, then the first step is check if an account is actually available on the system using getent.
getent passwd uucp
The getent utility requests entries from the Name Service Switch (NSS) libraries. This includes password files, group files, DNS resolving (including /etc/hosts ), etc.
Check processes running as a user
If the account exists, we should also check if any process is running under the ID.
ps aux | grep "^uucp"
If this reveals any process, the account appears to be still active. If this is a service account, it might be of legitimate use. If it is an old colleague, then it is time to determine what is running and see if it can safely be stopped.
Check files owned by a user
Next step is making sure that no files are owned by the user account. The easiest way is to use the find command and start searching on the root file system.
find / -xdev -user uucp
By using -xdev we tell find not to switch to other file systems. It is better to check them manually, before it starts searching all mount points (like your NFS shares!).
Delete user account
When no more files or processes are in use, you can delete the account with the deluser command.
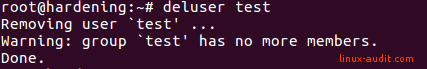
Conclusion
Unused Linux accounts are common. This is especially true with most Linux distributions, which deliver service accounts as part of a default installation. With a good approach it is easy to determine which users are still needed. By using password expiration for normal users, we can more easily detect which accounts are no longer needed and remove them.
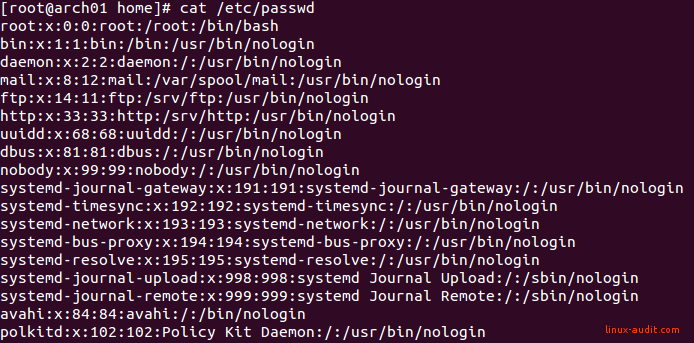
Arch Linux has a pristine list of service accounts, not much to clean
Happy hardening!
