Software Patch Management for Maximum Linux Security
Maximum Linux security with proper software patch management
Software upgrades are almost as old as the first lines of software code. Still companies struggle to properly update software, also when it comes to security patching. In this article we have a look at the reason behind patching and some methods to keep your systems humming, with fresh packages.
Why Update?
To most of us, it instantly makes sense to keep the software on your systems up-to-date. But still, sometimes we have to explain others why we do actually need a process to apply software updates and patches.
The most important reasons to keep software up-to-date are:
- Fixes to known software bugs
- Enhancements (new features or small improvements)
- Solve security issues and vulnerabilities
Linux Software
Each Linux based system is running the Linux kernel, together with supporting tools. These tools are collected by the distribution you are running. It is the vendor of this distribution which is responsible for tracking software updates. Depending on how “aggressive” the Linux distribution is, it may include many packages and updates, or be more conservative.
Bleeding Edge VS Stable
Arch Linux is one in the first group, being “bleeding edge”. It is much more progressive to include newer software packages. Red Hat on the other hand wants their customers to run very stable machines. Therefore they won’t add new features to an existing version, however will solve major bugs and security vulnerabilities. The result is older versions of the same software packages. Both have their advantages and clearly their disadvantages. In any case, all distributions have to track security updates, so they can provide patches.
Management Tools
For Linux patch management there are several different tools available. In categories they would be:
- Manual Patching
- Shell Scripts
- Automation & Configuration Tools
- Software Management Tools
Manual Patching
The most basic form of security patching is by hand. Simply running commands like apt-get update and yum update. The clear disadvantage is that this form is the most time consuming. This form of patching is prone to mistakes, as each system is different, especially with a stacked up amount of patches.
Shell Scripts
The next level of patching is using small scripts. It could be a small script, which automates several steps of the patching process. By distributing the same script to multiple machines, it ensures some level of repeatability, which equals quality.
Automation & Configuration tools
Tools like Ansible, Chef or Puppet can help with automating the security patch management. Simply feed the tool an update command, or what minimum version a software package should be.
Software management tools
Last but not least, most Linux vendors provide their own solution for managing software packages. It shows the installed packages and marks what packages have a security bulletin attached. Ubuntu has Landscape
product, Red Hat has Satellite
(see screenshot below).
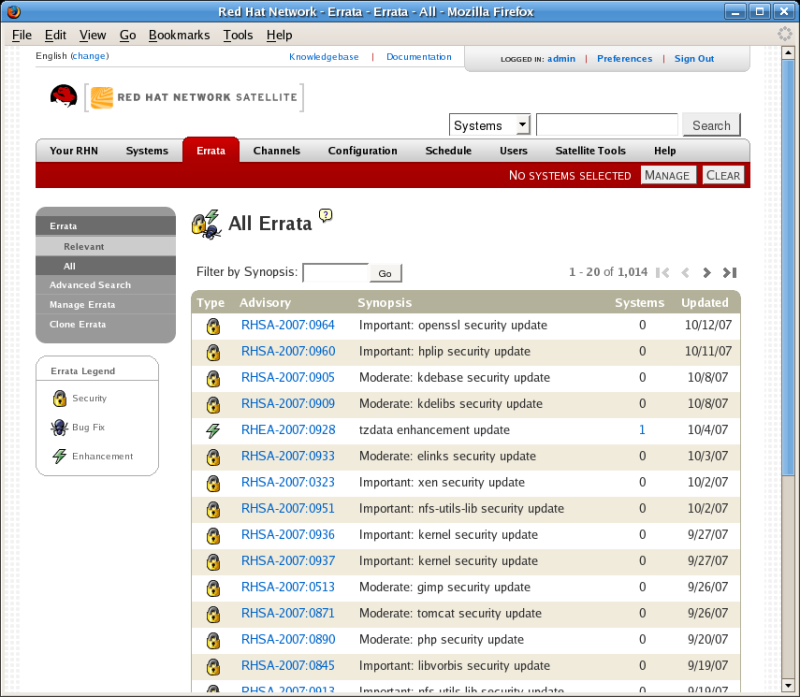
Patch management solution from Red Hat
Security updates
Depending on your situation, you might want to subscribe to a security related mailing list. This might be a generic one tracking software on Linux, or even a distribution specific list for security. Even if you have your patch management automated, you might want to perform regular audits. A small adjustment in your network configuration might result in non-patched systems, which with the right tool can be easily detected.
Automatic updating
Most package managers support automatic updating, or have supporting tools available to make this possible. For example the unattended-upgrades package helps to keep Debian/Ubuntu up-to-date. It is even possible to define what repositories should be used, so you give it a “security updates only” policy.

