Showing Available Security Updates with DNF
This article has last been updated at .
Checking Security Updates for your Software Packages
DNF is the default package manager since Fedora 22. As it is considered to be a better version of YUM, some of our Lynis users asked for DNF support. With focus on auditing and security patching, we definitely wanted to see that for ourselves. While building support, I’ve gathered the most important commands. In this blog post we will have a look how we can leverage the DNF output to show only the available security updates.
Check for Updates
The first step is to check if there are updates. With the check-update parameter we tell DNF to refresh its database and determine if there are any updates available.
dnf check-update
Showing DNF Security Updates
Next step is to determine if there are security notices available. This can be done with the updateinfo parameter.
dnf updateinfo
This command will tell us how many security updates it has found. Unfortunately, it does not reveal the specific packages involved. To get this information, we need to do a more specific query. By adding “list sec”, we can tell it to list only the security related updates.
dnf -q updateinfo list sec
Your output might look something like:
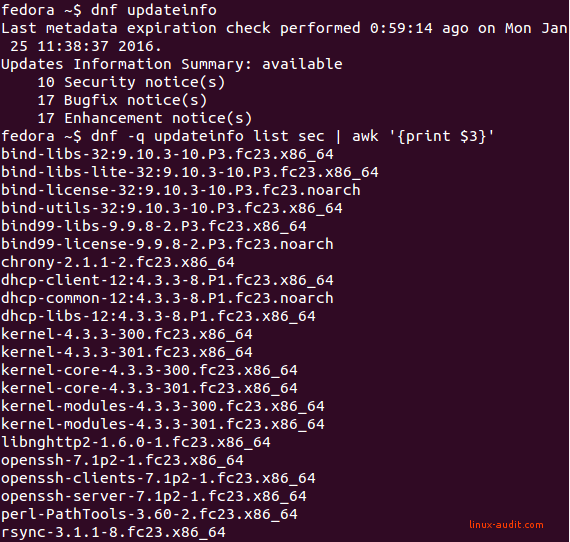
DNF in action
In this case, the Fedora server found 10 security notices. The number of packages might be higher, as some packages are related to each other (e.g. several instances for bind, dhcp, kernel, openssh).
The beauty of DNF is that you can run it as a non-privileged user. So if you are building automated tests, no need to use root permissions.
More Automation!
If you want to perform an in-depth security scan, you might be happy to know that initial Lynis patches have been applied to support DNF. It will gather installed packages, vulnerable packages, and perform an integrity check of the package database.
Any of the commands (not) working for you? Let it know!
