Security Integration: Configuration Management and Auditing
This article has last been updated at .
Increased strength when combining tools for automation and security of IT environments
Tools like Ansible, Chef, and Puppet are used a lot for rapid deployment and keeping systems properly configured. These tools in itself are great for ensuring consistency over your systems.
So what is Configuration Management?
Configuration management is the art of keeping systems properly configured. Usually companies start small, which equals manual configuration. Each time a new system is deployed, it is configured manually. While there is nothing wrong with this, it becomes an issue when systems are not kept up-to-date.
The earlier mentioned tools help with orchestrating how systems should be configured. This ranges from installed packages, up to specific configuration settings. Even software patching can be performed, simplifying the process of keeping systems up-to-date.
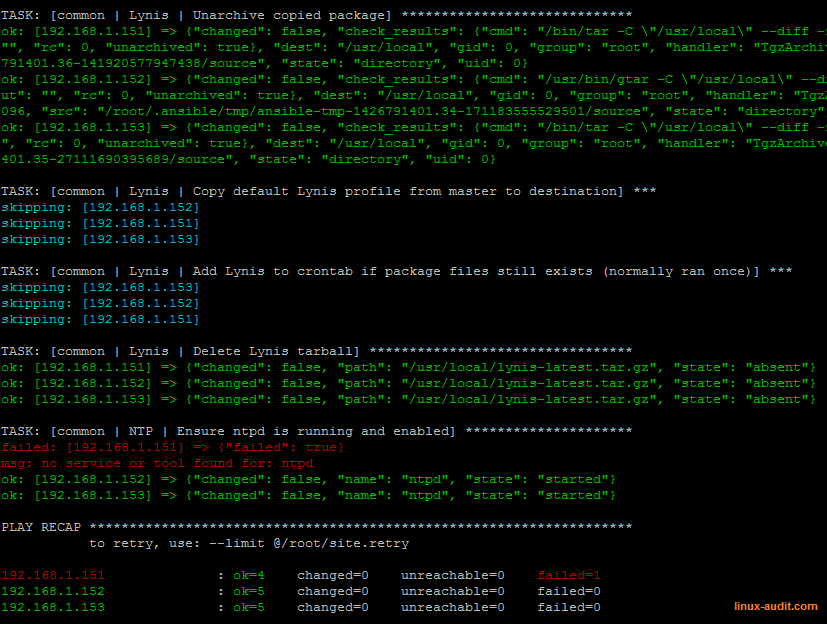
Example output of Ansible automation tool
Configuration management: When to Use?
The best moment to start using configuration management tools, is when you realized systems are different (while they were not supposed to be). Usually starting from 20-25 systems and upwards, automation of configurations will beneficial in the long term.
Speed
Another clear benefit is the speed of deployment. After all, almost no manual steps are needed. So environments which rely on this speed, are definitely a good candidate to use configuration automation.
Diversity
Companies with a lot of diversity in their operating systems, might have less benefit from configuration management tools. After all, a lot of exceptional configurations have to be made, specifying different ways to get the same result. Even the smallest action like installing a package, is a totally different set of commands between each operating system.
Picking the right tool(s)
When it comes to the differences in automation tools, there are several important areas. These are mainly the underlying programming language, the structure of files, and the way the communication occurs between the central server and the agents.
Personal preference
Usually a lot comes to the preference of the system administrator, which has to use the tool. If he/she has a strong preference for Python, a tool like Ansible might be more attractive. This simplifies installation (e.g. using pip), but also when implementing more advanced scripts. Sometimes the logic of the underlying programming language is visible there.
When selecting a tool, we suggest to have a look at the following attributes:
- Pricing
- Community support
- Availability of snippets
- Simplicity of tooling, website and documentation
- Preference of programming language
Security Automation
Configuration management tools are also great on supporting security objectives. One area might be system hardening, in which the tooling ensures that some settings are always enforced. Even if a system administrator or developer changes a setting, it will be reversed into the preferred setting.
Continuous Auditing
By combining configuration management and auditing, we can close the loop of automation. It enables us to perform configuration management, continuous auditing, and security monitoring at the same time. Most of the gaps will be closed by one tool, while the other one keeps an eye on existing and new risks. If for some reason something can be tuned, it will show up on the auditing side. It will be then an easy step to feed this as input and auto correct the issue.
Deploying an auditing tool
It should be a surprise that also an auditing tool could be deployed automatically. In the screenshot we can see how our auditing tool Lynis is installed. After installation it will be also configured and scheduled for execution. In our case we close the loop even further, by uploading the data to a central node, and monitor for regular audits. If the central system does not receive data for a few days, something is wrong and need attention. In other words, it equals a failure somewhere in a the chain. Only then we need to do a manual check. This type of automation prevents “ghost” systems, and solves malfunctioning systems or software, which otherwise would get noticed after months…
In the upcoming time we will definitely blog some more about automation and auditing.
