Protect against ptrace of processes: kernel.yama.ptrace_scope
This article has last been updated at .
Hardening the kernel with kernel.yama.ptrace_scope
Ptrace is a great troubleshooting tool for developers to determine how a process functions. It can be used to find programming flaws, like memory leakage. On the other hand, the tool also be used by people with malicious intent. For example to debug a process as a non-privileged user and find the contents of application memory.
Yama
Linux has the ability to include Linux Security Modules, to provide additional features with the means of a module. Yama does Discretionary Access Control of some kernel related functions, like defining if process tracing (ptrace) is allowed.
kernel.yama.ptrace_scope
The parameter kernel.yama.ptrace_scope helps system administrators to select what processes can be debugged with ptrace.
We can determine the active value with sysctl or using the pseudo file system /proc and find the related key.
# sysctl kernel.yama.ptrace_scope
kernel.yama.ptrace_scope = 1
Or query the /proc file system.
# cat /proc/sys/kernel/yama/ptrace_scope
1
For this particular key there are four valid options: 0-3
| kernel.yama.ptrace_scope value | Meaning |
|---|---|
| 0 | All processes can be debugged, as long as they have same uid. This is the classical way of how ptracing worked. |
| 1 | Only a parent process can be debugged. |
| 2 | Only admin can use ptrace, as it required CAP_SYS_PTRACE capability. |
| 3 | No processes may be traced with ptrace. Once set, a reboot is needed to enable ptracing again. |
Using Ptrace - Advice
Yama LSM enforcing enabled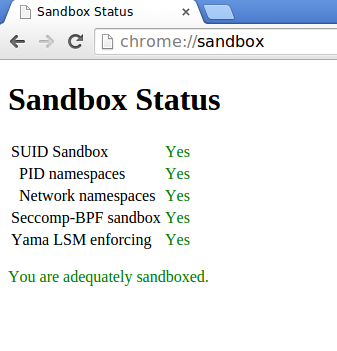
Servers
If your system is running in the DMZ and processes high sensitive data, there is usually no reason to allow ptrace at all. Best is to disable it completely (kernel.yama.ptrace_scope = 3).
For servers in general you might want to apply rule, or choose a slightly less restrictive value (2 or 1).
Desktops
On desktop systems where you are the only user, can have a less restricted option (2, 1 or even disabled).
The Yama LSM is also used in Google Chrome, as can been seen in the related screenshot.
If you want to dive deeper into the details of this LSM, have a look at Yama Linux Security Module
.
