Perform NetBSD security audit with pkg_admin
This article has last been updated at .
Security audit of NetBSD software packages with pkg_admin
NetBSD is especially known for it’s diverse platforms it can run on. What is less known is the ability to audit the installed packages. In this article we have a look on how to audit NetBSD and ensure the file integrity of your packages. Performing a security audit is easy, as long as you use the right tool!
Packages
When using packages, their metadata will be installed in directory within /var/db/pkg. This tree contains information about the packages.
netbsd# cd /var/db/pkg
netbsd# ls -l
total 146
drwxr-xr-x 2 root wheel 512 Dec 3 17:23 atf-0.20
drwxr-xr-x 2 root wheel 512 Nov 24 2013 libidn-1.28
-rw-r--r-- 1 root wheel 106391 Dec 3 17:07 pkg-vulnerabilities
drwxr-xr-x 2 root wheel 512 Nov 24 2013 pkg_install-20130902
-rw-r--r-- 1 root wheel 28672 Dec 3 17:23 pkgdb.byfile.db
drwxr-xr-x 2 root wheel 512 Nov 24 2013 pkgin-0.6.4nb1
drwxr-xr-x 2 root wheel 512 Dec 3 17:23 shtk-1.4
drwxr-xr-x 2 root wheel 512 Dec 3 17:23 sysupgrade-1.5nb1
drwxr-xr-x 2 root wheel 512 Dec 3 17:13 wget-1.14nb3
This directory can also contain a file named pkg-vulnerabilities. This file contains information about software vulnerabilities and can be used to check what installed software packages are vulnerable.
Moving deeper
When we look into the subdirectories within /var/db/pkgs, we see a structured format of files, which include the actual metadata about the package.
# ls -l
total 78
-r--r--r-- 1 root wheel 3455 Nov 24 2013 +BUILD_INFO
-r--r--r-- 1 root wheel 398 Nov 24 2013 +BUILD_VERSION
-r--r--r-- 1 root wheel 46 Nov 24 2013 +COMMENT
-rw-r--r-- 1 root wheel 3784 Nov 24 2013 +CONTENTS
-r-xr-xr-x 1 root wheel 4075 Nov 24 2013 +DEINSTALL
-r--r--r-- 1 root wheel 530 Nov 24 2013 +DESC
-rwxr-xr-x 1 root wheel 9090 Nov 24 2013 +DIRS
-rwxr-xr-x 1 root wheel 11075 Nov 24 2013 +FILES
-rwxr-xr-x 1 root wheel 2838 Nov 24 2013 +INFO_FILES
-r-xr-xr-x 1 root wheel 28793 Nov 24 2013 +INSTALL
-r--r--r-- 1 root wheel 8 Nov 24 2013 +SIZE_ALL
-r--r--r-- 1 root wheel 8 Nov 24 2013 +SIZE_PKG
Besides normal information (like a version number), there are actually some shell scripts. Mostly they deal with the directories, files and permissions.
Install pkg-vulnerabilities file
Before checking the system, it will need the pkg-vulnerabilities file. Installing is as easy as running the pkg_admin tool with the fetch-pkg-vulnerabilities parameter.
pkg_admin fetch-pkg-vulnerabilities
Checking the integrity of the vulnerabilities file
The pkg_admin tool is also able to check the integrity of the fetched file. Normally it should show no output, meaning everything is fine. If not, something like this shows up:
# pkg_admin check-pkg-vulnerabilities /var/db/pkg/pkg-vulnerabilities
pkg_admin: SHA1 hash doesn't match
Running vulnerability scan
With the audit parameter we can start a vulnerability scan. It perform a security audit on the installed packages. Every package which matches a specific version, will be flagged.
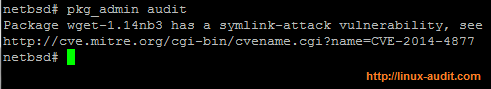
Discovered vulnerability in wget after running audit
Integrity check
Another thing the pkg_admin tool can perform, is an integrity check of the installed files. It uses the metadata from the packages directory and compares them with the actual files on disk.
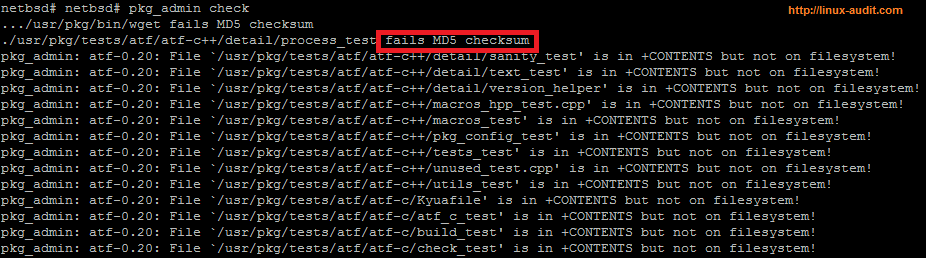
pkg_admin discovered mismatches during file integrity check
This small NetBSD utility is very nifty tool and a sign that NetBSD is taking security serious as well. Happy auditing!

