Linux Audit: Auditing the Network Configuration
This article has last been updated at .
Within this article we have a look on how to audit and check the network configuration of Linux and other systems. The main focus is on gathering information and discover how systems are configured. By taking these steps we will do a manual audit. For efficiency reasons we suggest to use an automated tool like Lynis.
Where to start?
Each Linux distribution has their own way and files to configure the network. Therefore we look at the basic components needed to configure a system. Usually the most important components are:
- Network interfaces
- IP address
- Netmask
- Gateway
- DNS configuration
- Hostname
The first two determine to which network segment a system belongs to. The configuration of the gateway address instructs the system on how to reach systems outside its own segment. The DNS configuration itself and the hostname, are used for resolving system names into IP addresses and back.
Nowadays the ip command is the preferred method to gather information, so we will use that as much as possible.
Network interfaces
Every system needs an IP address on the network to be able to communicate to other systems. On a link level there are no IP addresses involved yet. By using the ip link command we can see what links are up:
# ip link
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 16436 qdisc noqueue state UNKNOWN
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 00:16:db:dc:f7:97 brd ff:ff:ff:ff:ff:ff
3: wlan0: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN qlen 1000
link/ether 00:1c:d3:d1:c7:e8 brd ff:ff:ff:ff:ff:ff
Within this output we see a local loopback address (lo), a normal network interface card (eth0) and a wireless interface. The latter has a state of “DOWN”, meaning it’s not configured or disabled.
To see just the network interfaces itself, systems running systemd can use networkctl to display these.
# networkctl
IDX LINK TYPE OPERATIONAL SETUP
1 lo loopback n/a n/a
2 enp0s3 ether n/a n/a
2 links listed.
Routing
When a system wants to access another system outside the local network, it will use the default gateway to find a route to its destination. Depending on the internal routing configured, only a default gateway might exist.
# ip route
default via 192.168.1.1 dev eth0 metric 100
192.168.1.0/24 dev eth0 proto kernel scope link src 192.168.1.20
Alternative command is route -n, which will display similar information.
What to look for are the default route and any other possible routes. Systems in the same network zone should normally have a similar routing configuration. Exceptions might exist and should be investigated.
Resolving
To allow a system resolving hostnames into IP addresses (and back), DNS entries have to be configured. Usually this occurs in the file /etc/resolv.conf and is done with the nameserver option.
# cat /etc/resolv.conf
nameserver 8.8.8.8
nameserver 8.8.4.4
What to look for:
- At least two or more DNS entries configured.
- Test if the given DNS entries work properly
Lynis can automate these tests for you.
Hostname
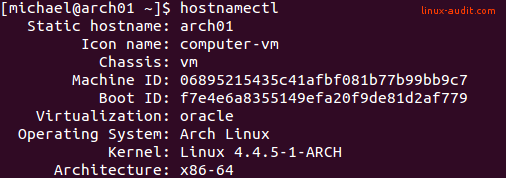
The hostname usually stored in /etc/hostname , or in the configuration file of the related network interface. By using commands like hostname or hostnamectl, it is easy to find the hostname of the system.
Automation
With all the differences between Linux distributions, systems like OpenBSD and FreeBSD and other Unix based systems (AIX, HP-UX, Solaris), manually auditing is time-consuming. Where possible it should be limited to a minimum and only focusing on the exceptions.
Common files
- /etc/resolv.conf
- /etc/network/interfaces
- /etc/sysconfig/network
Useful commands
- ifconfig
- ip
- route
