Kernel hardening: Disable and blacklist Linux modules
This article has last been updated at .
The Linux kernel is modular, which makes it more flexible than monolithic kernels. New functionality can be easily added to a run kernel, by loading the related module. While that is great, it can also be misused. You can think of loading malicious modules (e.g. rootkits), or unauthorized access to the server and copy data via a USB port. In our previous article about kernel modules, we looked at how to prevent loading any module. In this case, we specifically disallow the ones we don’t want.
Blacklisting modules
Blacklisting modules is one way to disallow them. This defines which modules should no longer be loaded. However, it will only limit the loading of modules during the boot process. You can still load a module manually after booting.
Blacklisting a module is simple. Create a file in the /etc/modprobe.d directory and give it a proper name (e.g. blacklist-module.conf).
Blacklisting firewire
Let’s say we want to blacklist firewire. We first have to determine what modules are available. By using find, we can quickly determine the related kernel drivers:
# find /lib/modules/`uname -r` -name *firewire*
/lib/modules/4.0.1-1-ARCH/kernel/drivers/firewire
/lib/modules/4.0.1-1-ARCH/kernel/drivers/firewire/firewire-ohci.ko.gz
/lib/modules/4.0.1-1-ARCH/kernel/drivers/firewire/firewire-core.ko.gz
/lib/modules/4.0.1-1-ARCH/kernel/drivers/firewire/firewire-sbp2.ko.gz
/lib/modules/4.0.1-1-ARCH/kernel/drivers/firewire/firewire-net.ko.gz
/lib/modules/4.0.1-1-ARCH/kernel/drivers/media/firewire
/lib/modules/4.0.1-1-ARCH/kernel/drivers/staging/fwserial/firewire-serial.ko.gz
/lib/modules/4.0.1-1-ARCH/kernel/sound/firewire
/lib/modules/4.0.1-1-ARCH/kernel/sound/firewire/snd-firewire-lib.ko.gz
Now we know there are multiple modules, most part of the drivers and one in the sound section. If we want to disable all these modules, we could simply blacklist them all. Or block the generic category.
Gathering module information
By using modinfo, we can gather the details about a particular module. In this case, we have a look at the snd-firewire-lib module and see what it does:
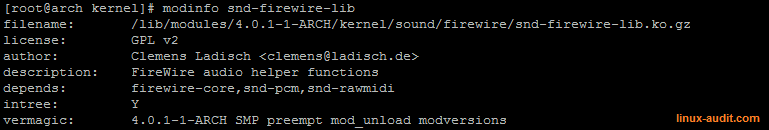
The modinfo commands shows on which a module depends
We can see it depends on firewire-core. Let’s have a look at the firewire-core module itself:
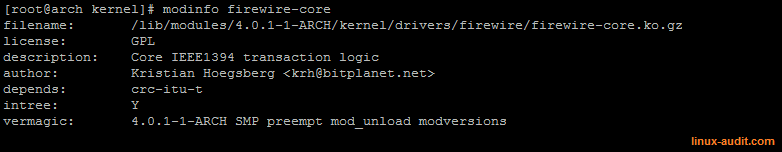
Details of firewire core module
The details of the firewire-core module show that is responsible for firewire itself. It is the core unit itself and doing the transaction logic within the IEEE1394 protocol specifications. We can see it is depending on the CRC-ITU-T standard.
By blacklisting the firewire-core, we effectively disable any module depending on it. In this case, we don’t blacklist the crc-itu-t module, to prevent other modules from properly functioning.
The related snippet to blacklist would be:
/etc/modprobe.d/blacklist-firewire.conf
blacklist firewire-core
See blacklisted modules
To see what modules are currently blacklisted, we can use the modprobe command:
# modprobe --showconfig | grep blacklist
blacklist firewire_core
This will show all modules which are blacklisted.
Disable modules
The next level of blacklisting modules is to actually disable them. This way they won’t be loaded unintentionally.
To disable a module, we have to redirect a module via the install option. Modprobe will try to load the related file. By defining a module as /bin/true, it won’t be loaded.
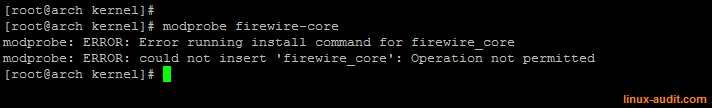
Using the install option we can avoid loading modules
To see what modules are currently disabled via install, we can use modprobe as well:
# modprobe --showconfig | grep "^install" | grep "/bin"
install firewire_core /bin/true
install firewire_ohci /bin/true
Note: the root user can still override settings, by using the -ignore-install parameter. In that case, the module can still be loaded.
Besides the install routine, there is also an alias option. This might be used to redirect a module to /dev/null for example.
Conclusion
By using the right combination of blacklist, install and alias, we can disallow the loading of Linux kernel modules. They form the first level of defense against unintentional and unauthorized module loading. By using the kernel setting kernel.modules_disabled and set its value to 1, we can make sure things are really tightened. Even the root user can not load any modules anymore.
Useful commands
When working with kernel modules, here are some of the most common commands:
- Blacklisted and disabled modules
- modprobe -showconfig | egrep “^(blacklist|install)”
- Find modules
- find /lib/modules/`uname -r` -print
- Show loaded modules
- lsmod
- Load module
- modprobe module
- Unload module
- modprobe -r module
- Module details
- modinfo module
Questions or other tips? Let it know!

