How to solve Shellshock on Debian and Ubuntu
This article has last been updated at .
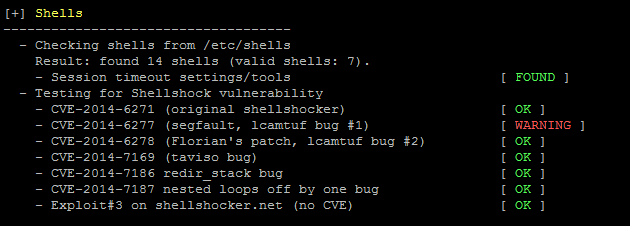
Shellshock tests for bash in auditing tool Lynis
Shellshock
is a serious software weakness, or vulnerability, in Bash. This shell is used on almost all Unix based systems, including Debian and Ubuntu. As it can be used without much effort and remotely exploit systems, it has a maximum vulnerability score according to CVSS
.
Upgrade Bash
First update the software repository with apt-get, using the update parameter.
apt update && apt install -only-upgrade bash
Your system should now have a newer version of bash. You can check this by using ls -l /bin/bash and see the date of the binary. Additionally, use dpkg -s bash to see package details and the version. Also the changelog of the package will give additional insights regarding the package and what has been done in the latest version.
Show changelog:
apt changelog bash
Unattended upgrades
To keep up-to-date automatically, use the unattended-upgrades package.
Installation
Installation is by using apt-get, like you would normally do when using software packages on Debian and Ubuntu.
apt install unattended-upgrades
Configuration
The only thing which needs to be configured is the configuration file. The package itself includes the following files:
/etc/pm/sleep.d/10_unattended-upgrades-hibernate
/etc/logrotate.d/unattended-upgrades
/etc/init.d/unattended-upgrades
/etc/apt/apt.conf.d/50unattended-upgrades
The last file is the configuration file and you want to check if it includes the security updates.
// Automatically upgrade packages from these (origin:archive) pairs
Unattended-Upgrade::Allowed-Origins {
"${distro_id}:${distro_codename}-security";
// "${distro_id}:${distro_codename}-updates";
// "${distro_id}:${distro_codename}-proposed";
// "${distro_id}:${distro_codename}-backports";
};
Within this configuration file, you can decide to do more upgrades unattended, depending on the type of system and your personal preference. After configuration, check if the package has been executed the day after. It will log its activities in /var/log/unattended-upgrades/unattended-upgrades.log. Additional actions are available in the same directory, in separate log files.
