How to solve an expired key (KEYEXPIRED) with apt
This article has last been updated at .
Software updates and package management is easy with systems based on Debian or Ubuntu. Just apt-get update (or apt update) and run an upgrade. But sometimes you may encounter the following situation: a KEYEXPIRED message.
KEYEXPIRED message
# apt-get update && apt-get upgrade
Get:1 http://security.ubuntu.com/ubuntu xenial-security InRelease [94.5 kB]
Hit:2 http://nl.archive.ubuntu.com/ubuntu xenial InRelease
Get:3 http://nl.archive.ubuntu.com/ubuntu xenial-updates InRelease [95.7 kB]
Hit:4 http://nl.archive.ubuntu.com/ubuntu xenial-backports InRelease
Hit:5 https://packages.cisofy.com/community/lynis/deb stable InRelease
Get:6 http://nl.archive.ubuntu.com/ubuntu xenial-updates/main amd64 Packages [373 kB]
Ign:7 http://nginx.org/packages/mainline/ubuntu xenial InRelease
Get:8 http://nginx.org/packages/mainline/ubuntu xenial Release [2,309 B]
Get:9 http://nginx.org/packages/mainline/ubuntu xenial Release.gpg [287 B]
Get:10 http://nl.archive.ubuntu.com/ubuntu xenial-updates/main i386 Packages [368 kB]
Get:11 http://nl.archive.ubuntu.com/ubuntu xenial-updates/universe amd64 Packages [319 kB]
Get:12 http://nl.archive.ubuntu.com/ubuntu xenial-updates/universe i386 Packages [316 kB]
Err:9 http://nginx.org/packages/mainline/ubuntu xenial Release.gpg
The following signatures were invalid: KEYEXPIRED 1471427554
Fetched 1,566 kB in 0s (2,003 kB/s)
Reading package lists... Done
W: An error occurred during the signature verification. The repository is not updated and the previous index files will be used. GPG error: http://nginx.org/packages/mainline/ubuntu xenial Release: The following signatures were invalid: KEYEXPIRED 1471427554
W: Failed to fetch http://nginx.org/packages/mainline/ubuntu/dists/xenial/Release.gpg The following signatures were invalid: **KEYEXPIRED** 1471427554
W: Some index files failed to download. They have been ignored, or old ones used instead.
Reading package lists... Done
Building dependency tree
Reading state information... Done
Calculating upgrade... Done
The following packages will be upgraded:
apparmor libapparmor-perl libapparmor1 python3-distupgrade python3-software-properties software-properties-common ubuntu-release-upgrader-core
7 upgraded, 0 newly installed, 0 to remove and 0 not upgraded.
Need to get 0 B/672 kB of archives.
After this operation, 5,120 B of additional disk space will be used.
Do you want to continue? [Y/n] y
The KEYEXPIRED shows that validation failed on the related repository signature. This is a good thing, to warn us that we should be checking the repository. With an expired key, the solution is simple: we need to download an updated key. Apparently it is for the nginx repository.
Step 1: Run apt-key
Using the apt-key utility we can display all the known keys.
apt-key list
In our case, we see the nginx key is expired a few days ago:
pub 2048R/7BD9BF62 2011-08-19 [expired: 2016-08-17]
uid nginx signing key signing-key@nginx.com
Two items are highlighted in this example. The first one is the short version of the key. The second one is showing that the key is expired (including the date). This key was valid for almost 5 years.
To quickly find the expired keys, search for “expired:”:
apt-key list | grep "expired:"
Step 2: Update the key
We can now use the key gathered in step 1 to update it:
apt-key adv --keyserver keys.gnupg.net --recv-keys [KEY]
The output might look like this:
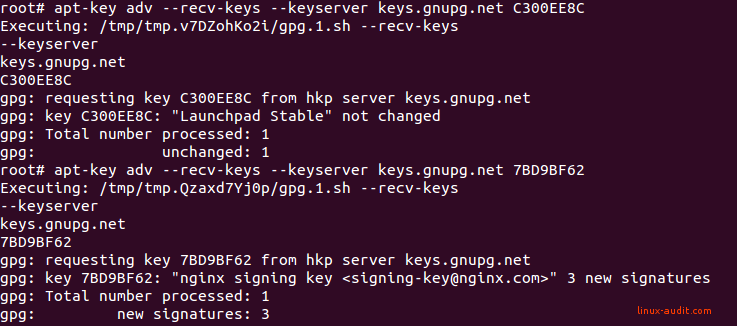
The key is renewed, after choosing the right one (otherwise no change is made)
On purpose we selected an incorrect key, which was also related to nginx:
/etc/apt/trusted.gpg.d/nginx-development.gpg
pub 1024R/C300EE8C 2010-07-21
uid Launchpad Stable
As you can see in the output above, nothing happens when you select the wrong key.
Step 3: Update
After renewing the expired key you can run apt update again and install any available upgrades.
apt update && apt upgrade
Happy upgrading!
