How to clear the ARP cache on Linux?
This article has last been updated at .
There are several reasons when you might need to clear your ARP cache. There are two common ways on Linux systems, typically using the arp or ip utility. Depending on your Linux distribution and the availability, we suggest using the ip tool.
Clearing cache with ip
Newer Linux distributions have the ip utility. The ip tool has a more advanced way to clear out the full ARP cache.
ip -s -s neigh flush all
The first -s will provide a more verbose output. By adding one more, we can select the neighbor table. The neighbor table with the ip command equals both the ARP and NDISC cache. Note that the -s options are not available on all versions of the ip command. If it not supported for your version of ip, then simply remove them from the command.
The output of the flush all command will produce the following output.
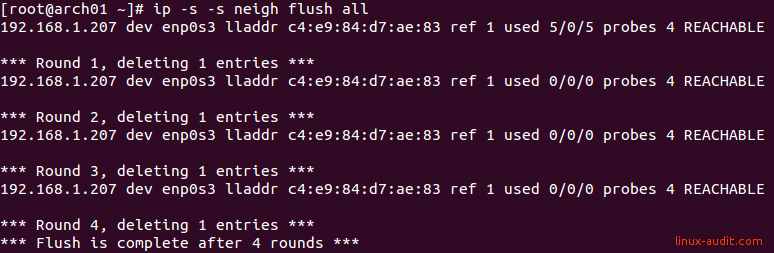
The ARP cache is cleared, with verbose output
Clearing cache with arp command
The arp utility does not accept an option to clear the full cache. Instead, it allows to flush out entries found with the -d option.
arp -d 192.168.1.1
After deleting, have a look with the arp utility again to see the new list:
arp -n
The output of this command will typically show the active ARP entries.
Address HWtype HWaddress Flags Mask Iface
192.168.1.1 (incomplete) eth0
192.168.1.2 ether 00:02:9b:a2:d3:f3 C eth0
192.168.1.3 ether 00:02:9b:d9:d1:a2 C eth0
The 192.168.1.1 entry now shows as incomplete, which means the ARP entry will be refreshed when it is needed again.
Conclusion
Depending on your distribution, the ip utility is quicker if you want to flush out the full ARP cache. For individual entries, the arp tool will do the job as quickly. Both tools are available for most distributions, including Arch Linux, CentOS, Debian, Fedora, RHEL, and Ubuntu.
Did this article to clear the ARP cache help you as well? Wonderful! Become part of the community and share this on social media to let others know. Got questions or suggestions? Let it know!
