How to use grep (with examples)
This article has last been updated at .
The grep command is one of the oldest tools for Linux and other platforms. Actually, it is older than Linux itself. It was written by Ken Thompson more than 45 years ago! The name grep stands for “globally regular expression print”. This name comes from its predecessor ed and the specific mode in which you would globally search, using a regular expression, and print the output. The related command was “g/re/p”. For more history, have a look at the Wikipedia
entry. Otherwise, let’s dive into the tool and get to know some practical grep examples for daily usage.
Introduction
One of the reasons to create this blog post is that there are a lot of examples available for the grep command. But with all information scattered, most people don’t take the time to really learn the most basic commands. We want to leverage the full potential of the grep command, as it can be used in many work-related or personal related activities. It is common to use it for checking configuration files and searching through log files.
Why learn the grep command and regular expressions?
As with every tool, it is often easy to start using it, but hard to really master it. The man page is very extensive, so is the online help documentation. Although these sources are a great reference, we will be showing the grep command by example. And we will include specific use-cases which are common for system administrators and security professionals. Especially if you have to deal often with data, investing some time in doing things efficiently will pay off.
Before you continue
If you are using grep on another platform than Linux, you may not have the GNU version of grep. Some things in this guide may not be working, or need specific tailoring. You can easily find out what version you have with grep --version.
Need a particular job to be done with the grep command and can’t get it to work? Use the comments and share what you have tried. Let’s start with the basics and become a ‘grep master’.
Basic usage examples of grep
Use grep for simple actions
The grep utility does not need much to starts doing its work. The syntax of grep consists of four parts.
- grep command
- optional: option(s)
- string to search
- file, files, or path to be searched
The options that grep uses typically have a long and short format. The long format has two dashes, followed by a word or words. Use the long format when using them in scripts, so that it becomes obvious what the grep command is doing. Use the short notation in your daily tasks and on the command line, to save on typing and speed up your work.
If you would like to find the root user in your /etc/passwd file, just tell it to search for ‘root’ and the file name itself. In this case, no option is needed.
grep root /etc/passwd
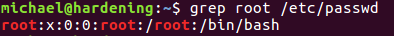
Using colored grep output
If the command above did not show colored output on your system, you might want to enable that. It can be done with --color auto. As this would mean you have to type it in each time, using an alias would save you from a lot of typing.
alias grep='grep --color=auto'
You can add this alias to your .bash_aliases or .bashrc file if you are using the bash shell. Otherwise, add it to the respective profile file. These files can be found in your home directory.
Ignore case sensitivity
Now that we have performed a basic grep command, we can start to change its behavior. Often we already know the word or words we are looking for. What we don’t always know is if one or more occurrences of the word are using capitals. By default, the grep command will be case-sensitive. So only the right match will be displayed. We can tell grep to ignore case-sensitive searches with the -ioption.
grep -i root /etc/passwd
Show line numbers
Depending on your search, you may have many occurrences of the text you were searching for. Use the -n option to have grep show the related line numbers.
grep -n root /etc/passwd
Excluding words
To exclude particular words or lines, use the -invert-match option. Use grep -v as a shorter alternative. Exclude multiple words with grep by adding -E and use a pipe (|) to define the specific words. Optionally make it case insensitive with the -i as listed above.
grep -i -v -E 'banana|monkey' zoo.txt
Match counting
It may be useful to know the number of occurrences of your specified word. This count is displayed when using grep -c or grep -c -v to show the number of non-matching lines.
grep -c monkey zoo.txt
Recursive search through directories and files
To search in one directory, there are the -r and -R options to achieve this. Depending on the target and the existence of symlinks, you might want to use the first one if you do not want to follow them. Use the capitalized option, grep -R, if you want to include any possible symlinked file to be searched as well. This may take much longer and could result in other file systems to be searched as well.
grep -r password /etc
Tip: if you don’t want the filenames in the output, add the -h option.
Show matching files only
Sometimes you just want to see the files that match a particular text string. There is the grep -l command to do achieve this.
grep -l -R password /etc
To show all files that do not match your target, use the capitalized version: grep -L.
Using regular expressions
The grep utility is a powerful tool and can use regular expressions. Regular expressions can be considered ’logic rules’ for matching text strings. Think of something like “I know the word should be starting with the letter ‘a’, but after that everything is fine”. By using a regular expression we can express this in short notation (e.g. "a.*").
Match specific words only
You may be searching for a very short, yet specific word. In this case, grep will return way too many results. By using more specific statements we can limit the output.
grep "\bbin\b" /etc/passwd
The \b tells grep to use word boundaries.
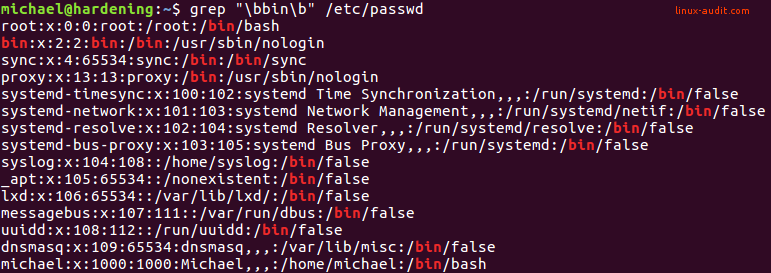
Although you could use spaces to search for a full word, that often won’t give you the right result. It will return some hits, while it might be missing a few as well. For example, any occurrences at the begin or end of the file. There will also be no match if any special characters are followed by it, or even a simple character like a comma.
Tip: use the -w(--word-regexp) option to achieve the same as this regular expression above, as it is easier to remember.
Find lines starting with a specific string
With the carrot symbol (^) we can activate a regular expression that defines that the line should start with a specific piece of text.
grep "^systemd" /etc/passwd
Find lines ending with a specific string
Like the carrot symbol, we can use the dollar sign ($) to mark the end. Only lines that match that, will be returned. A great way to find all accounts that have a particular shell configured.
grep "bin/bash$" /etc/passwd
Search for multiple words
Sometimes you want to match multiple words. By using parentheses you can tell grep to search for one word, or the other. Each possible match is split by a pipe sign.
grep -E "^(backup|root|syslog)" /etc/passwd
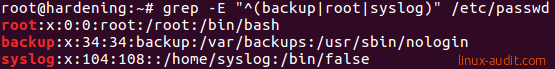
Matching multiple words
Note: use the -E option to enable extended regular expressions. Without it, the command won’t give any results.
Combining grep with other tools
Exit code
Using grep in your shell scripts can be very useful. For example, you can use it to determine if a particular file has the right configuration setting and then perform an action based on that. Another one is to see if a particular user exists in your /etc/passwd file.
grep -q michael /etc/passwd
Grep will not display anything, but end with an exit code. This exit code will be stored in a special variable with the name $?. If you want to see it on the command line, use it with echo.
echo $?
Exit codes:
- 0 = match found
- 1 = no match found
- 2 = error
Example syntax to use grep in your shell script:
if $(grep -q michael /etc/passwd); then echo "Michael is in passwd file"; else echo "Michael is not in passwd file"; fi
Using pipes
The grep command is a great utility to use in combination and filter the output of other commands. This way the screen only shows that data you are interested in. To achieve this we use the pipe sign (|) to tell the shell to send any output to the next command in line.
It is common to apply multiple grep commands by piping them together. When using big data files, try to limit the number of pipes to increase performance. You may also want to look for alternative solutions when you are repeating them often.
Example: Search in dmesg output
The dmesg command gives a lot of lines as output. If we are just interested in information regarding our storage, we can easily do by searching for “sd”.
dmesg | grep sd
If we just would like to find AppArmor related events, it would make sense to ignore case due to the capitals in the name. By smart combining the right tools, we can form a powerful data filter.
dmesg | grep -i apparmor
Advanced tips
Improve search speed: fixed strings
Typically you may be using already a specific word that you want to be matched. When searching through big files, grep may take a while to complete its task. By using the -F (fixed strings) option this can be dramatically improved. The only downside is that regular expressions can not be used.
Searching inside compressed data (avoid using gunzip!)
Need to search inside compressed files? Use the zgrep command. It has the same syntax and it knows how to deal with compressed data.
Conclusion
The grep command is a very powerful tool and easy to work with. To truly master it, one should be learning more about regular expressions. It makes searching and finding the right data much easier. Knowledge about regular expressions will also come in handy for other tools, like sed and awk. If you really want to learn how to use the grep command, use it daily and create your own list of commands you often use.
Do you have a great one-liner that you often use with grep? Share it and we see if it can be included!
