FreeBSD hardening with Lynis
Lynis
development has its roots on a FreeBSD
system, therefore FreeBSD hardening is also easy and supported when using Lynis. People who want to audit and harden their FreeBSD system will discover Lynis to be a powerful tool for this purpose. In this article we will focus on how to audit your system with Lynis.
Ports
Lynis is available from the ports tree
and usually the version is close or at the latest version. To install Lynis this way:
cd /usr/ports/security/lynis/ && make install clean
or to add the package:
pkg install security/lynis
In case the Lynis version from the ports tree is not up-to-date, please create an issue on Bugzilla
for the port. In the meantime you could download Lynis manually from the CISOfy website and extract the tarball in a temporary directory.
Running Lynis
Running Lynis can be as simple as using the audit command to perform a scan with all tests enabled. Any tests that are not relevant for FreeBSD will be skipped.
lynis audit system
The output might look something like this:
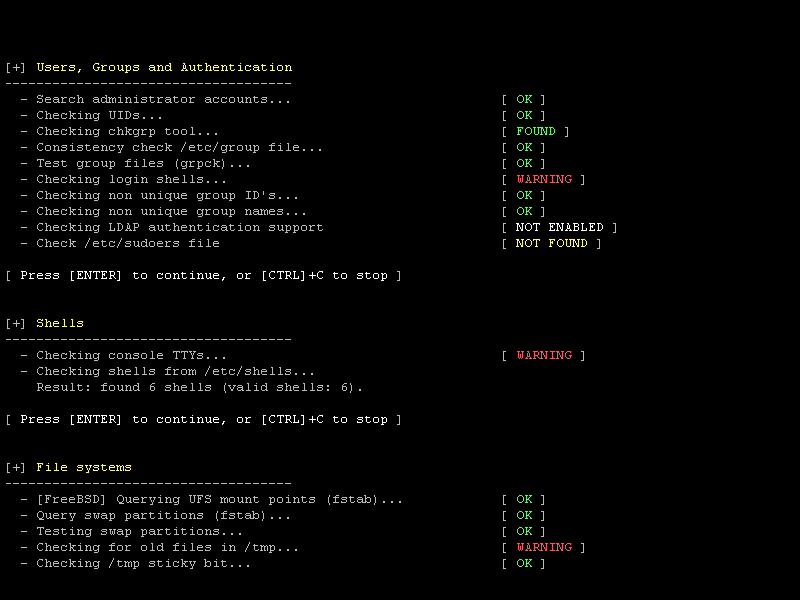
Screenshot of security scan performed with Lynis
Note: if you manually unpacked the tarball, use
./lynis audit systemfrom the local directory instead.
Usually FreeBSD installations are already pretty well hardened out of the box, as the installation requires you to install additional software. Still, it’s worth to perform an extensive audit and check the outcome of the tests. These will be displayed at the bottom of the screen, together with a hardening index and pointers to log file and report file.
After the scan you are advised to have a look at the log file (default /var/log/lynis.log) to determine what has been checked in each test and any further suggestions. Warnings and suggestions will be displayed also on screen.

