Finding boot logs in systemd journals
This article has last been updated at .
Systemd used a binary log to store information about specific events. These events include the boot sequence and the related output. In this article we have a look at finding our boot logs in systemd journals.
Binary logging
When using systemd, boot data is stored in journals, a binary format. There is big benefit of saving boot data in a binary format: log information of each boot can be stored separately, linked to other pieces of information, and queried easier and quicker. For example, different boots can be compared, as they are individually available.
The journal can be queried with the journalctl command. When using the --list-boots parameter, we get a list of entries which each represent a different system boot.
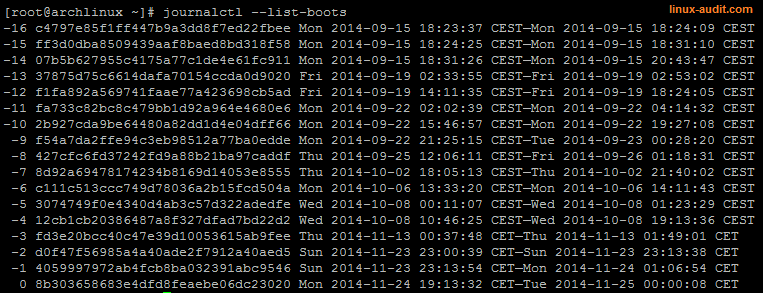
Output of journalctl --list-boots
In this output the first column is the reference ID. The last entry on screen (ID equals zero) is the active boot. The utility will give each boot a (negative) number to show how many boots is was ago.
The second field is the boot ID. These first two IDs can be used when referring to a specific boot. Next there is the day, date, time and timezone, when the first entry entered the journal. These are then followed by the same fields, representing the last entry of the journal.
With these references, we can now see the details of a specific boot by using the reference ID or boot ID itself.
journalctl --boot=fa733c82bc8c479bb1d92a964e4680e6
