File permissions of the /etc/shadow password file
This article has last been updated at .
The password files are an important cornerstone of the security of your Linux system. Commonly they are /etc/passwd and /etc/shadow . Sometimes we receive questions what the right permissions of these files should be. Therefore this blog post to have a look at the file permissions (and ownership) of both files.
Passwd file
The password file stores local accounts of the system. It is a readable text file and uses colons (:) to separate the fields. In this file the account names, identifiers, and other descriptive fields are stored. This file helps with converting user IDs to names (and back).
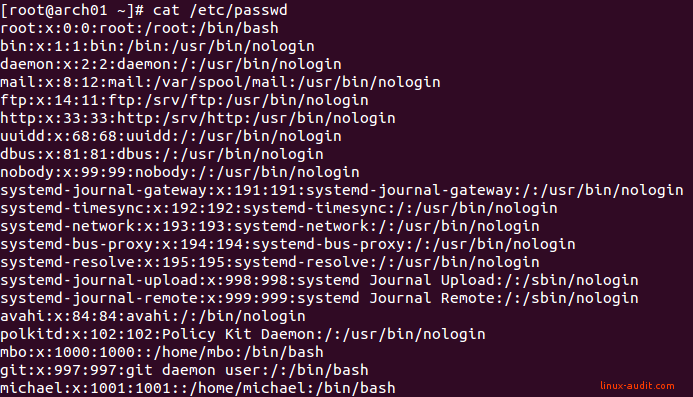
Example output of a /etc/passwd file on Linux
Fun fact: some systems which have this file broken (or their authentication like LDAP), will get something like
I have no name!
You don’t want to end up being a number ;-)
Permissions of /etc/passwd
While it is fine that all users can read this file, they should not be able to change fields. Otherwise it could disrupt file permissions and authorizations. It would be fairly easy to take over the root account for example.
# ls -l /etc/passwd
-rw-r--r-- 1 root root 1046 Oct 27 16:05 /etc/passwd
This file typically has no other special file permissions, like an immutable bit.
Shadow file
Like the passwd file, the /etc/shadow file inherits most of the same fields and values:
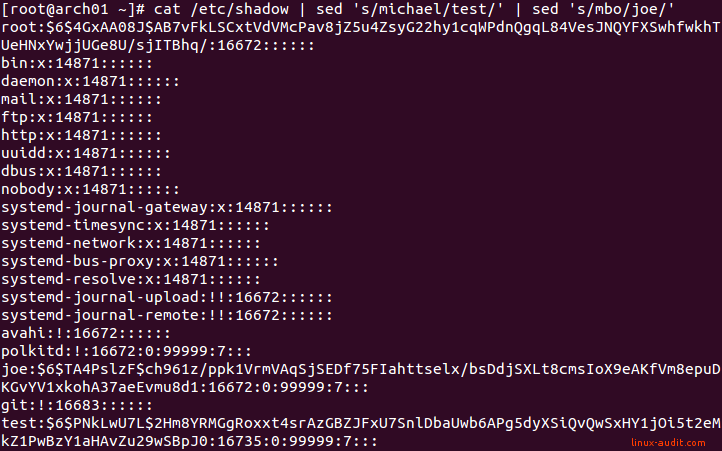
Example of /etc/shadow and encrypted passwords
One big exception with the passwd file, is the password itself. So in other words, the password is not stored in /etc/passwd, but in /etc/shadow. It is stored as a long string of characters, which is a combination of the hashing algorithm, optional salt applied, and the hashed password itself. If you are new to the subject, then consider a hash like a fingerprint of the password, but not the real content. So you can always check again the rightful owner of the password, without storing it unencrypted. The salt value adds more randomness to the mix. This forces attackers to use a brute force attack on a much bigger set of possible values.
Permissions of /etc/shadow
The owner of the /etc/shadow file is usually the user root. The group is often set to an administrative group, like shadow. Other users are not allowed to read the file directly, to prevent them from gathering hashes passwords of others. With a tool like passwd, which has a setUID bit, the file can be altered in a controlled way.
# ls -l /etc/shadow
-rw------- 1 root root 823 Dec 7 19:59 /etc/shadow
Issues
Commonly when people have made changes to the files, issues arise. Your password files could be damaged, or have altered file permissions. If that is the case, compare the permissions with another system and correct them. If you didn’t make changes to the system, consider that your system may have been compromised by an intruder. In that case, we suggest further analysis and a reinstall of the system.
Did this article help you fixing your file permissions? Let it know!

