Configure the minimum password length on Linux systems
This article has last been updated at .
Linux and password strength
One of the options to improve password security is by setting a minimum length. This prevents users from choosing easy passwords. As part of Linux system hardening, you don’t want your passwords to be cracked too quickly by modern password crackers.
Configuration
Let’s have a look at how to configure password security and in particular the length and its strength.
Login settings
The first area where you can set a password length is in /etc/login.defs . The related setting is PASS_MINLEN and already tells us it is about the minimum length of a password. Modern Linux distributions will no longer use this setting and prefer PAM, or pluggable authentication modules.
It started with cracklib (PAM)
Maybe the first module for configuring password settings was the cracklib module. Primary focus was on testing passwords, preventing users from choosing too simple passwords. With the configuration options it provides, it allows the administrator to define a password policy. One of these items is the minimum password length. Other settings include the usage of special characters, like the usage of capitals and numbers.
Next is pwquality (PAM)
Based upon the foundation of Cracklib, the pwquality module has similar functionality. It is backwards compatible with pam_cracklib.
The related configuration file is /etc/security/pwquality.conf .
Minimum length is not length
When we talk about length, a small note should be made. Both modules related to PAM have a specific meaning when it comes to the minimum length. It is a computed value and includes complexity factors from the password itself. For example if and how many capitals, numbers, or special characters it has. To use the minimum length properly, you also have to configure the other settings.
Configuration differences between distributions
Each distribution uses their own files when it comes to PAM. Here is an overview of the common locations where you can find the PAM configuration files and specifically the setting related to the minimum password length.
- Arch Linux: /etc/pam.d/system-auth with pam_pwquality, or per service.
- CentOS 7: Using /etc/pam.d/system-auth (symlink) and /etc/pam.d/password-auth (symlink) with pam_pwquality
- Fedora: /etc/pam.d/system-auth-ac with related lines starting with “password”
- Gentoo: /etc/pam.d/system-auth using pam_cracklib
- RHEL 6: /etc/pam.d/passwd using pam_cracklib
- RHEL 7: /etc/pam.d/passwd using pam_pwquality
- Ubuntu: /etc/pam.d/common-password using pam_pwquality with the minlen setting.
Your Linux distribution or version missing? Share your feedback.
If you only want to enforce password complexity on authentication done via SSH, then use the /etc/pam.d/sshd file. If that doesn’t exist on your distribution, search for ssh in the /etc/pam.d directory.
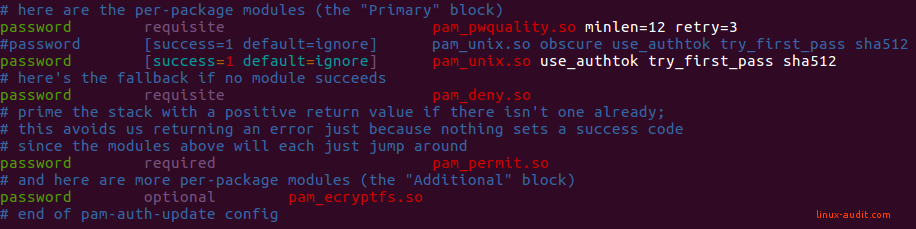
Configuring PAM should be done with care
When using the pwquality module, there is a separate configuration file available. This file is /etc/security/pwquality.conf and can also be used for the configuration. We suggest picking this one and document it properly. If you would use both options, you might end up with differences. For example, the passwd tool may then use a different setting than other tools or routines.
Testing your passwords and their strength
After tuning the configuration of your system, you may want to test if the changes were properly implemented. There are a few ways to test for this. The first one is using the passwd command and simply change a password of a test user. Try using simple passwords and slightly longer or complicated variations.
A better method might be using the pwscore tool, that is part of the pwquality tools package (libpwquality-tools). Start the tool and type in a password to have it tested. Good to know is that this tool uses its configuration from the file /etc/security/pwsecurity.conf . If you set a minlen value via PAM, it might not be picked up.
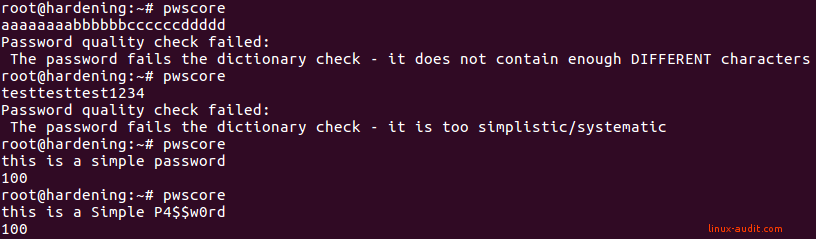
Sometimes simple but long passwords may score high. That doesn't make them secure!
Got other tips for our readers? Let it know!
