Password Security with Linux /etc/shadow file
This article has last been updated at .
Linux systems use a password file to store accounts, commonly available as /etc/passwd . For additional safety measures, a shadow copy of this file is used which includes the passwords of your users. Or actually hashed password, for maximum security. This shadow file is /etc/shadow and has line like this:
username:$6$6Y/fI1nx$zQJj6AH9asTNfhxV7NoVgxByJyE.rVKK6tKXiOGNCfWBsrTGY7wtC6Cep6co9eVNkRFrpK6koXs1NU3AZQF8v/:16092:0:99999:7:::
For proper display, let’s split this up in several fields:
- username
- $6$6Y/fI1nx$zQJj6AH9asTNfhxV7NoVgxByJyE.rVKK6tK
- 16092
- 0
- 99999
- 7
- empty
- empty
Field explanations
Time to have a look what all these strings mean:
1) Username
The first field is an easy one, it is the username of the particular account.
2) Password hashing details + hashed password
The most important string in the /etc/shadow file is definitely the second field. It includes the password details and consists of several parts. In this case it starts with ‘$6$’, which refers to SHA-512.
Note: if the password field just has a ! or *, then the account is locked. A double ! (!!) indicates a password has never been set.
Schemes overview
| Identifier | Scheme |
|---|---|
| 1 | md5crypt |
| 2, 2a, 2b, 2x, 2y | bcrypt |
| 3 | NTHASH |
| 5 | sha256crypt |
| 6 | sha512crypt |
| 7 | scrypt |
| 8 | PBKDF2 with different implementations |
| gy | gost-yescrypt |
| md5 | Solaris MD5 |
| sha1 | PBKDF1 with SHA-1 |
| y | yescrypt |
MD5
Indicated with ‘1’, usually MD5 with 22 characters.
SHA-256
Indicated with ‘5’, usually SHA-256 with 43 characters.
SHA-512
Indicated with ‘6’.
Second part is salt and separators (in this case $6Y/fI1nx$). The salt is a small string of characters to mix into the hashing function. Its goal is making it more difficult to perform certain password based attacks on the hashed password. This salt consists of characters a-z, A-Z, 0-9, / and .
Long string of characters = hashed password
The long string and its length depends on the hashing method used. With $6, or SHA-512, it will 86 characters.
Yescrypt
Indicated with a ‘y’. It has a number of rounds between 1-11, with the default being 5 rounds.
To see the number of rounds, look at the second string. For example: j9T=5 rounds, jAT=6 rounds, jBT=7 rounds, jCT=8 rounds, jDT=9 rounds, jET=10 rounds, jFT=11 rounds.
3) Last changed
This number indicates when the password was last changed. The number does indicate the day number, starting from epoch date (1 January 1970). Right now that is in the 16000+ range.
4) Number of days before password can be changed
This field defines how long it takes before the password can be changed. In our case zero, so it can be changed now.
5) Number of days till required password change
Another pretty self-explanatory field, stating how long is left (in days), before a password change is required. A great option to force password changes.
6) Warning threshold in days
In line with previous field it describes the number of days till a warning will be giving. In this example it is a week.
7) Expire date
Also stored in days, describing when the account was expired (from epoch date).
8) Reserved field
Usually not used by Linux distributions.
File Permissions
The /etc/shadow file should be owned by the root user, with usually shadow as group owner. This file should not be world-readable, therefore 640 or 400 would be an appropriate file permission.
Tips for reviewing the /etc/shadow file
By default the shadow file looks cryptic (pun intended). To simplify the output, one could use getent combined with awk and column It extracts all entries from the shadow database, extracts entries where the second field starts with a dollar sign ($), and finally presents it in a more friendly way.
getent shadow | awk -F: '$2 ~ /^\$/' | column --table --separator :$
Consistency checking of /etc/passwd and /etc/shadow
Linux distributions usually provide a pwck utility. This small utility will check the consistency of both files and state any specific issues. By specifying the -r it may run in read-only mode.
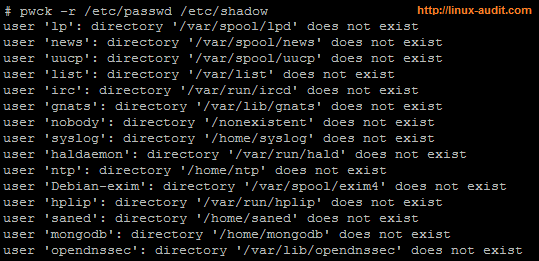
Example when running pwck on /etc/passwd and /etc/shadow file
Anything missing from this article? Let it know!

